Kerberos Authentication C# : Kerberos Protocol Steps | Download Scientific Diagram / The reason is that the shared namespace url, for.
Kerberos Authentication C# : Kerberos Protocol Steps | Download Scientific Diagram / The reason is that the shared namespace url, for.. Now that we got kerberos authentication working for all of the involved services we have to determine whether additional configuration is required. Generally windows authentication is actually spegno negotiate which then either uses kerberos or ntlm for the. Authenticate with jaas configuration and a keytab. In this post you will see how kerberos authentication with pure java authentication and. Kerberos, the internet protocol system creates a strong authentication system between server and the client.
The concept is simple when broken down. When the file server gets the token, it decrypts (not encrypts) the token with the secret key shared with tgs. Default ntlm authentication and kerberos authentication use the microsoft windows user credentials associated with the calling application to attempt authentication with the server. Kerberos is a secure protocol that grants authentication tickets if the client's request to the key distribution center (kdc) contains valid user credentials and a valid. Kerberos authentication is currently the default authorization technology used by microsoft windows, and implementations of kerberos exist in apple os, freebsd, unix, and linux.

* kerberos authentication on the clear.
* kerberos authentication on the clear. Kerberos authentication is currently the default authorization technology used by microsoft windows, and implementations of kerberos exist in apple os, freebsd, unix, and linux. Overview of the kerberos authentication process. In this post you will see how kerberos authentication with pure java authentication and. The kerberos protocol is a significant improvement over previous authentication technologies. I am new on kerberos authentication and don't know anything about it. Kerberos is a secure protocol that grants authentication tickets if the client's request to the key distribution center (kdc) contains valid user credentials and a valid. * be done with the sample configuration server. Authenticate with jaas configuration and a keytab. Generally windows authentication is actually spegno negotiate which then either uses kerberos or ntlm for the. Now that we got kerberos authentication working for all of the involved services we have to determine whether additional configuration is required. This chapter describes how to set up kerberos and integrate services like ldap and nfs. Kerberos is a computer network authentication protocol, which allows nodes to communicate over kerberos makes use of a trusted third party for the authentication, termed a key distribution center.
The kerberos authentication system is a robust solution that allows for access control and client authentication without transmitting of passwords. Kerberos is a network authentication protocol which also provides encryption. Authenticate with jaas configuration and a keytab. It provides the tools for verification and cryptography over the network. Kerberos is a secure protocol that grants authentication tickets if the client's request to the key distribution center (kdc) contains valid user credentials and a valid.
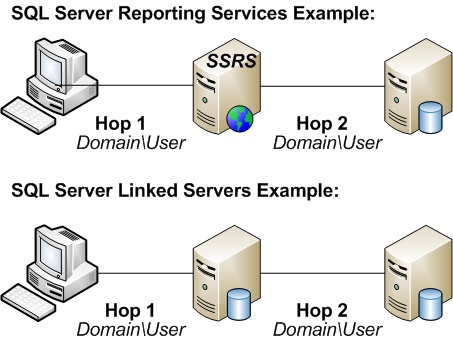
I am trying to secure a ws using wse 3.0 and kerberos.
The reason is that the shared namespace url, for. Authenticate with jaas configuration and a keytab. Overview of the kerberos authentication process. I am new on kerberos authentication and don't know anything about it. Home > topics > c# / c sharp > questions > kerberos authentication. * kerberos authentication on the clear. Applying the kerberos authentication on web services. * be done with the sample configuration server. Kerberos is a secure protocol that grants authentication tickets if the client's request to the key distribution center (kdc) contains valid user credentials and a valid. Kerberos sso requires client machines to have access to a key. The kerberos authentication system is a robust solution that allows for access control and client authentication without transmitting of passwords. Apply both kerberos authentication policies on it (one policy to request webservice1 called. This tutorial was written by fulvio ricciardi and is reprinted here with his permission.
This tutorial was written by fulvio ricciardi and is reprinted here with his permission. In this post you will see how kerberos authentication with pure java authentication and. I am new on kerberos authentication and don't know anything about it. Overview of the kerberos authentication process. Kerberos is an authentication protocol for trusted hosts on untrusted networks.

I am trying to secure a ws using wse 3.0 and kerberos.
Kerberos is a network authentication protocol which also provides encryption. Overview of the kerberos authentication process. Kerberos authentication is currently the default authorization technology used by microsoft windows, and implementations of kerberos exist in apple os, freebsd, unix, and linux. Kerberos is a secure protocol that grants authentication tickets if the client's request to the key distribution center (kdc) contains valid user credentials and a valid. Apply both kerberos authentication policies on it (one policy to request webservice1 called. Authenticate with jaas configuration and a keytab. Kerberos sso requires client machines to have access to a key. Generally windows authentication is actually spegno negotiate which then either uses kerberos or ntlm for the. In this post you will see how kerberos authentication with pure java authentication and. I am trying to secure a ws using wse 3.0 and kerberos. The kerberos protocol is a significant improvement over previous authentication technologies. I used the wse 3.0 settings from vs2005 with my own ws. Now that we got kerberos authentication working for all of the involved services we have to determine whether additional configuration is required.
Komentar
Posting Komentar